If you listen closely, you can hear the squeal of excitement from thousands of security fanatics across the nation as Verizon has recently released its 11th installment of the Data Breach Investigations Report (DBIR). If you are not one of those fanatics who read it cover to cover, don’t worry, we have you covered. Here are our top takeaways from the 2018 DBIR:
Summary of Findings
For those who don’t know, the DBIR is one of the most data-driven and unbiased annual security publication in the world, and this year’s report is no different.

While some findings repeat themselves year after year (e.g., employees are still your greatest vulnerability), there is some data that may surprise you. Below is a summary of key findings:
- Ransomware incidents doubled last year and is more often impacting critical data than in past years.
- Most companies receive malware on six or fewer days per year.
- Phishing is still the most common method of social attacking, but pretexting is on the rise (170 incidents, 114 confirmed data breaches)
- 13% of breaches featured phishing in some capacity.
- Distributed Denial of Service (DDoS) are becoming more frequent, but the median size of these attacks has dwindled to below a gigabit per second.
- Amplified DDoS attacks account for a much larger percentage of DDoS attacks than non-amplified.
- Denial of Service (DoS) is the most widely used technique in reported security incidents (21,409), while the use of stolen credentials accounts for the most widely used technique in security breaches (399).
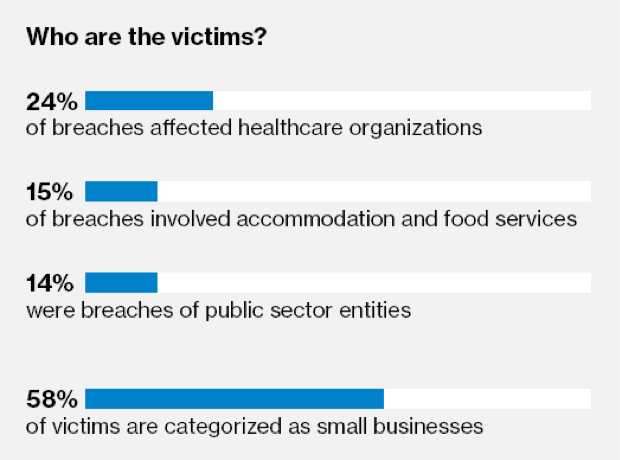
Who Fell Victim to Attack?
According to the findings, 58% of victims are categorized as small businesses, and 24% of breaches affected healthcare organizations.
Source: Verizon DBIR - Page 5
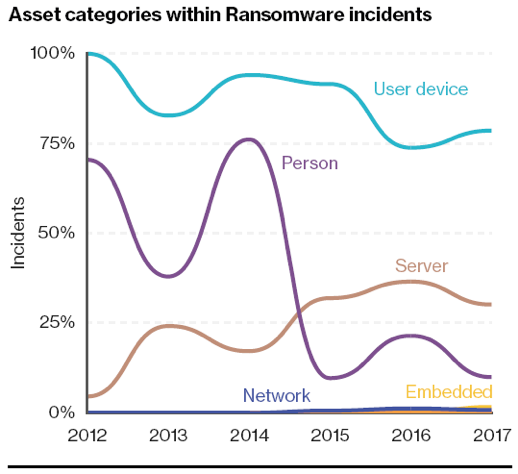
Dirty Deeds Done Dirt Cheap
Ransomware attacks (e.g., WannaCry, Petya) doubled last year, and considering they doubled in 2016 too, we can only hypothesize that attacks will continue to increase. These attackers can attempt infection with little risk and at virtually no cost, but receive a big payout. What’s even scarier is that ransomware attacks are showing more prevalence in infecting critical servers, which is far more damaging than just infecting a single user device.
Source: Verizon DBIR - Page 14
Curiosity Killed the Cat
Or, it prompted you to a click a malicious link in a fake email resulting in a malware infection. Called phishing, this technique is designed to influence the recipient to “take the bait” via a single mouse click embedded in a seemingly innocent email. This technique is often used as a lead action of a larger attack and is followed by other actions that ultimately lead the exfiltration of data. In fact, phishing accounted for 13% of breaches last year. However, there’s good news – when analyzing the data from phishing simulations, it showed 78% of people don’t click a single phishing email all year.
Although phishing is still the most common method of social attacking, pretexting is gaining ground. Using pretexting, attackers develop a dialogue with a victim to obtain information or influence behavior. In 2017, there were 170 incidents and 114 confirmed data breaches using this technique. Combined, phishing and pretexting represent 98% of social incidents and 93% of breaches.
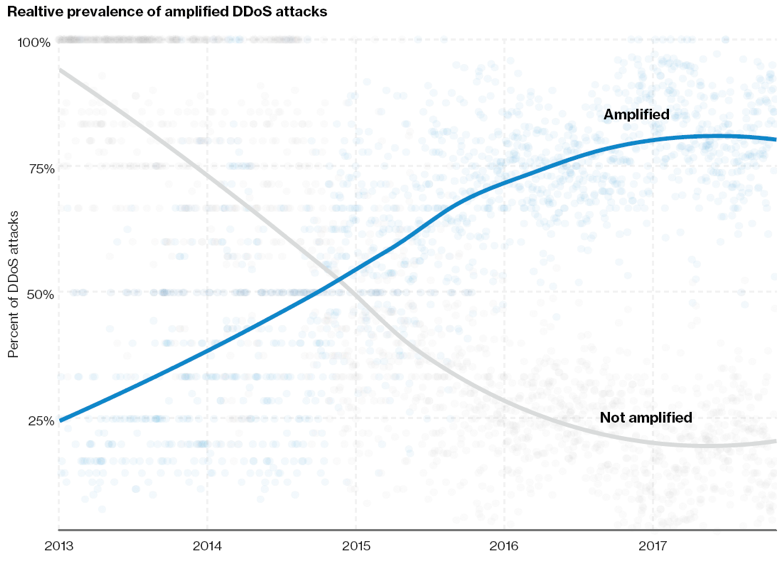
Amplified DDoS Attacks
Amplified DDoS attacks take advantage of the ability to send small spoofed packets to services that will reply back to the victim with a much larger response, effectively flooding it with requests to crash the connection. As the DBIR puts it: “It is similar to asking a friend ‘How are you?’ and then receiving a twenty-minute response about the price of gas, how much they love CrossFit™, their cat’s hairball problem, etc.” This attack technique is has grown significantly as compared to non-amplified attacks.
Source: Verizon DBIR - Page 21
How To Avoid Becoming A Statistic
Very few people look forward to this annual study more than my colleagues and I in the security industry. For us, this is a validation of an ever-evolving threat landscape that constantly modernizes itself and develops new tactics to impact and degrade businesses all over the globe. Let’s be honest – to those who may be hearing about this study for the first time, this information is daunting, overwhelming, and downright scary. We can be lead to think that we are powerless in the fight against these sophisticated attacks, but our brightest days our still ahead of us. There are simple things every organization can do TODAY to minimize their attack surface and lower their business risk through a renewed focus on cyber hygiene.
“The more things change, the more they stay the same.”
French Novelist, Jean-Baptiste Alphonse Karr, was almost certainly not predicting the rise and sustainability of current cyberattack vectors and trends almost 170 years after his famous quote, but he was on to something. Over the past few iterations of annual Verizon DBIR, we continue to see “the big 3” overarching attack trends year over year:
- Ransomware is on the rise
- Phishing attacks continue to dominate
- The human factor continues to be a weakness
The good news is that organizations can become incredibly resilient in their defense against those attack vectors by focusing on end user awareness and education, as well as more robust endpoint protection technologies that incorporate anti-ransomware defenses, AI deep learning modules, and cryptoguard defenses. And yet, as I write this, I am certain that I could probably just wait 12 months and cut and paste this final paragraph into our analysis of the 2019 Verizon DBIR, knowing that attackers will ONLY change their tactics once their current methods stop being fruitful. It is up to us to create a more risk-aware security culture and to enlist the help of qualified security professionals to fill those critical gaps within our organizations. History favors the prepared, and as we say at Dataprise: “We can’t make security easy, but we can make it simple.” Contact us to learn more about our anti-ransomware defenses and phishing simulation campaigns with realistic interactive training modules and let’s make the world better, together!
Click here to read the full Verizon report.